NIST Special Publication 800-37 Revision 2
The National Institute of Standards and Technology (NIST) released the NIST Special Publication 800-37 Revision 2 to help manage security and privacy risks in federal information systems. It explains the Risk Management Framework (RMF), which aligns with OMB Circular A-130 and supports mandates from the Federal Information Security Modernization Act (FISMA) and related executive orders.
The framework provides a cost-effective, structured approach to selecting, implementing, and monitoring security and privacy controls. It supports activities like security assessment, control authorizations, and ongoing authorization to operate.
With links to NIST SP 800-53, the RMF helps organizations manage vulnerabilities, meet compliance requirements, and safeguard critical infrastructure.
Now, let’s see how the RMF works in practice and how organizations can use it to enhance security across the full system lifecycle.
What Is NIST 800-37 Used For?
NIST Special Publication 800-37 provides federal agencies and information technology contractors a risk management framework for information systems. It outlines the RMF, a structured process for selecting, implementing, and monitoring security controls based on risk.
The goal is to make risk-based decisions throughout the system’s lifecycle, from design to decommissioning. While designed for federal use, private-sector organizations also apply the RMF to strengthen accountability.
What’s New in NIST SP 800-37 revision 2?
Released in 2018, Revision 2 of NIST SP 800-37 modernized the RMF. It introduced the following major enhancements.
- Executive-level integration: Aligns risk management with governance and strategic decision-making.
- Efficiency improvements: Streamlines RMF processes to reduce duplication and lower implementation costs.
- Alignment with NIST CSF: Bridges the RMF with the NIST Cybersecurity Framework for a unified approach.
- Privacy risk integration: Embeds privacy considerations directly into the risk management process.
- Supply chain risk management: Adds controls and guidance for evaluating third-party and vendor risks.
- Flexible control selection: Supports risk-based customization beyond standard control baselines.
NIST 800-37 vs. NIST 800-53
NIST Special Publication 800-53 is one of the most widely used catalogs of security and privacy controls. But how does it relate to NIST SP 800-37?
- NIST SP 800-37: Defines the RMF, a process for selecting, implementing, and managing those controls.
- NIST SP 800-53: Provides the actual control library used within that process.
Think of 800-37 as the “how” and 800-53 as the “what.” Together, they help organizations manage risk across the system lifecycle.
Core Components of NIST SP 800-37 R2
The RMF in NIST SP 800-37 Rev. 2 helps organizations manage security and privacy risks across information systems with leadership accountability and team-driven implementation. Below, we discuss the core components of the RMF.
Three-Tiered Structure
The RMF operates across three organizational levels:
- The first level prepares the organization by aligning risk management with strategic goals and governance.
- The second level focuses on mission and business processes, planning how RMF activities will be carried out.
- The third level applies the RMF to individual information systems, ensuring system-level risks are managed in line with higher-tier decisions.
Integrated Security and Privacy Programs
The RMF requires collaboration between information security and privacy. Security programs protect confidentiality, integrity, and availability at the system and data layers.
Privacy programs protect personally identifiable information (PII). They need to work together because when AI systems process PII, security alone isn’t enough. Active privacy controls are also needed for full protection.
System Boundaries and Shared Elements
Every RMF implementation defines a clear authorization boundary—the set of systems and components governed by the controls. These systems:
- Support the same business function
- Share similar security and privacy requirements
- Process, store, and transmit similar types of data
- Operate in the same technical environment
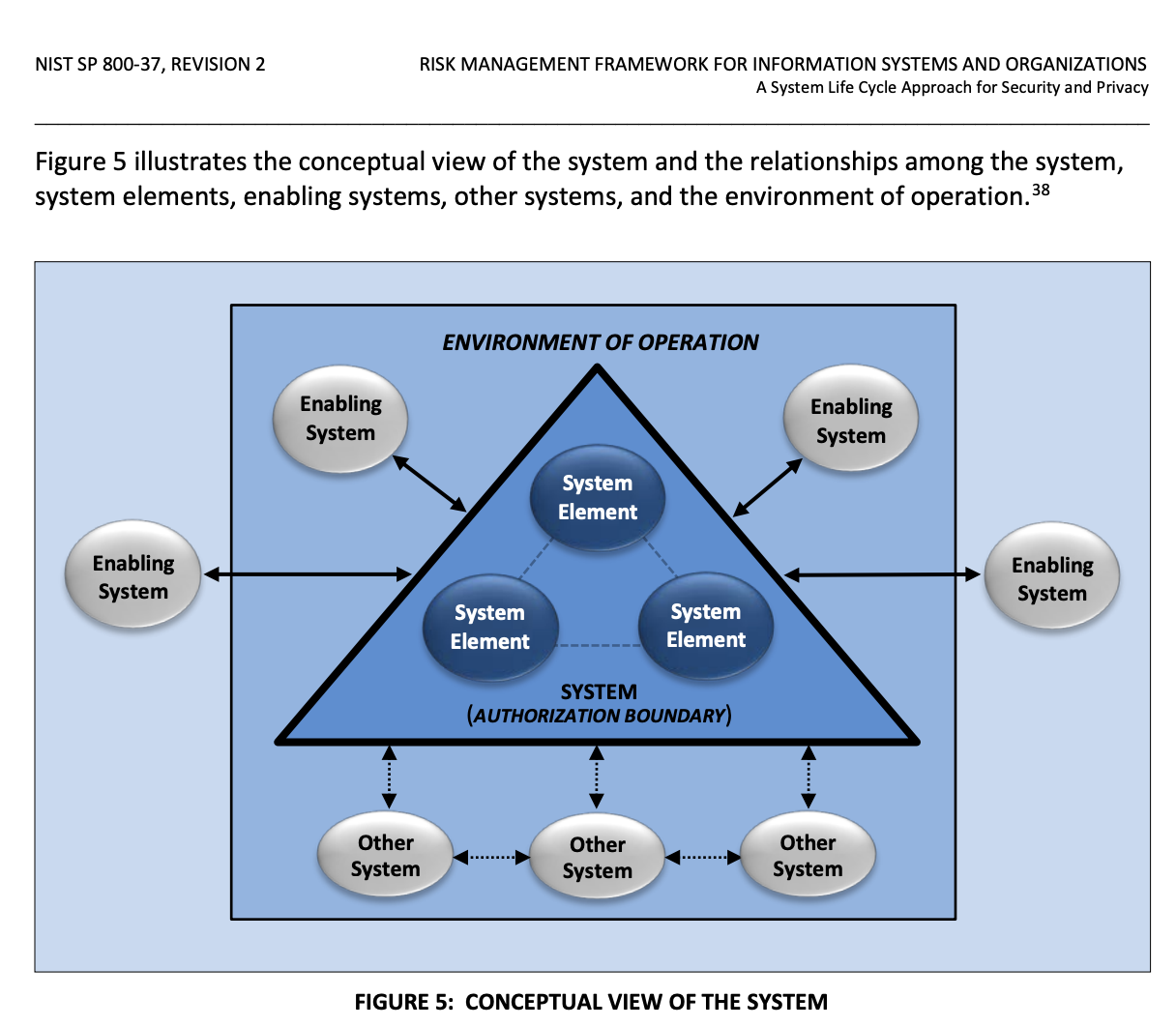
This diagram is taken directly from NIST SP 800-37 r2 and can be found at: https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-37r2.pdf
Controls
In the RMF, requirements define what you must achieve (e.g., legal or regulatory obligations), while controls define how to meet them.
Control catalogs such as the NIST Cybersecurity Framework translate these requirements into practical implementation across systems and data layers.
Security and Privacy Posture
An organization must define and maintain the posture of each system—its current state of security, privacy readiness, and risk exposure. This includes assigning common controls, assessing system health, and documenting how well the system can resist attacks.
Supply Chain Risk Management (SCRM)
The RMF now incorporates SCRM principles to address third-party risk management and working with external service providers.
As organizations rely more heavily on outsourcing, they must manage cybersecurity risk in the supply chain lifecycle.
The RMF and SCRM work together to reduce the potential impact from untrusted or compromised suppliers.
How to Execute the RMF Effectively
The RMF has seven core steps. Each is designed to help organizations manage cybersecurity architecture and privacy risks across the system development life cycle (SDLC).
- Prepare: Define business priorities, mission needs, and risk tolerance. This step aligns senior leaders and operations teams on what’s at stake.
- Categorize: Classify systems and data by their potential impact. Accurate categorization drives everything that follows.
- Select controls: Choose appropriate controls for the security risk level of the systems. Use NIST control baselines, but tailor them to the environment.
- Implement controls: Apply the controls. Make sure they’re embedded in technical workflows, not bolted on later.
- Assess controls: Test and validate. Ensure controls are effective, properly configured, and documented.
- Authorize: Decide whether the system’s risk is acceptable. Use security risk assessment results to support informed, accountable decisions.
- Monitor: Track performance over time. Monitor for changes in risk, system behavior, or control effectiveness. Update as needed.
Use ZenGRC to Simplify RMF Execution
ZenGRC simplifies the execution of NIST SP 800-37 by centralizing your control selection, risk assessments, and authorization workflows in one platform. It supports continuous monitoring, maps controls to NIST baselines like 800-53, and gives leadership real-time insight into system risk and compliance posture.
Schedule a demo to see how ZenGRC can strengthen your risk management strategy.
