Blog
Page 72 of 152
Cybersecurity Concerns in the Financial Services Sector
Over the last several years, the banking and financial services sectors have seen a huge increase in ransomware attacks and other cyber threats worldwide. This increase in cyberattacks has resulted from several factors: New opportunities for social engineering attacks resulting from the pandemic; Increased profitability of miner malware; Lack of scalable cybersecurity and information security […]

March 11, 2022
How to Apply Cybersecurity Measures to Reduce Risk
Hackers and cybercriminals constantly seek to circumvent your security systems and gain access to the sensitive data of your customers and staff. Hence the need to protect yourself from cyber-attacks. Indeed, cybersecurity must be part of every company’s plan for growth, regardless of whether you use advanced cloud computing or stick with email and maintaining […]

The Relationship Between Risk Appetite and Compliance
ISO Guide 73:2009 establishes a set of definitions for risk management in organizations. It defines risk appetite as “the amount and type of risk that an organization is willing to pursue or retain.” The concept refers to the acceptable level of risk within an enterprise risk management structure, understanding that risks are a fundamental part […]

How to Integrate Cybersecurity into Business Continuity Planning
Business continuity means keeping your business operations up and running despite disruptions: natural disasters, pandemics, cyber attacks, other technical issues, and more. Your business must always be operational for growth and sustainability. Of course every business has its own unique operations and practices, and those traits influence your specific business continuity plan. That said, all […]

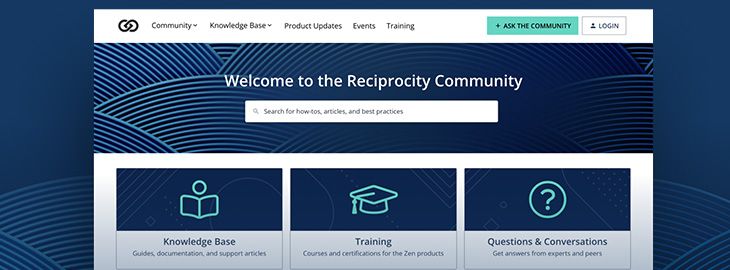
Introducing the New Reciprocity Community
By Leigh Ann WhitmarshDirector of Customer Experience, Reciprocity We are excited to introduce our new Reciprocity Community in support of the launch of our new Reciprocity ROAR platform. The new Reciprocity Community is a self-service, one-stop shop that helps customers succeed in achieving their risk and compliance goals. The Community provides access to all Reciprocity […]
March 10, 2022
What is Data Spillage and How to Address it
What Is Data Spillage and How to Address it Key Takeaway Data spillage happens when confidential information is accidentally released into an unauthorized environment. It’s usually because of human error, not a malicious attack. Organizations can prevent data spills with strong security controls, limited access, encryption, and employee training. Table of Contents Key Terms Data […]

March 9, 2022
Domain Hijacking: What Is it & How to Protect Your Organization
Domain hijacking is a form of cybersquatting premised on changing a domain name system (DNS) registration without its original domain registrant’s authorization, or on abusing privileges on DNS hosting provider accounts. Domain hijacks have been used to steal traffic from high-traffic websites through phishing and other social engineering tactics. Domain name hijacking is a chronic […]

IT Risk Management: A Primer on Policy, Examples, Best Practices
Enterprise risk management (ERM) should be a core component of every company’s overall business strategy. To maintain operations, you need to be prepared for any potential threats that may occur. Moreover, ERM should extend to all areas of your company, including IT. Cybersecurity risks are potentially devastating, yet also challenging to track and predict; which […]

Reciprocity Introduces Industry’s First AI-Powered, Integrated Cyber Risk Platform
Reciprocity’s Pioneering New Approach to Risk Management Enables Companies to Avoid, Control, and Mitigate Risk in Business Processes While Providing Clear, Executive-Level Visibility Into Risk SAN FRANCISCO, Calif. – March 8, 2022 – Reciprocity, a leader in information security risk and compliance, today announced its new AI-powered, integrated Risk Observation, Assessment, and Remediation (ROAR) Platform, […]

March 8, 2022
From the Back Office to the Boardroom: The Changing Role of the Security Executive
By Rob Ellis SVP of Product Strategy Get this White Paper CISOs and other security executives have long been perceived as the “no” people of the organization. When new ideas, tools, or proposals reach their desk (often late in the game), many security executives have taken the approach of shutting them down due to concerns […]
![[White Paper] From the Back Office to the Boardroom: The Changing Role of the Security Executive](https://www.zengrc.com/wp-content/uploads/2024/11/whitepaper_changing-role-security-exec_featured-img_730x270.jpg)
Page 72 of 152
